The First Unconditionally-Secure File Transfer in Romania powered by OTP & QKD - June 2023 @ UPB
File Transfer Using OTP enhanced by QKD
The Transmission Protocol
The One-Time Pad (OTP) encryption method is known for its impeccable security profile when implemented correctly.
Each bit or character from the plaintext is encrypted by a modular addition with a bit or character from a
secret random key or 'pad' of the same length. This results in the ciphertext, which is then sent over an insecure channel.
The receiver, possessing an identical copy of the key, can reverse the process and decrypt the message.
Given the keys are truly random, as long as the plaintext, used only once, and kept completely secret, the OTP is unbreakable,
providing perfect secrecy.
However, the challenge lies in securely distributing these keys. This is where Quantum Key Distribution (QKD) comes into play, leveraging the principles of quantum mechanics to share cryptographic keys between two parties in a way that any eavesdropping attempts can be detected. In a typical QKD protocol, two parties, commonly referred to as Alice and Bob, can create shared random keys. In case a third party, Eve, attempts to intercept these keys, her actions will invariably introduce detectable anomalies due to the Heisenberg Uncertainty Principle.
Integrating OTP with QKD, we get an encryption scheme that is not only theoretically secure but also practically secure against key distribution attacks. This is because, in the quantum world, the act of measuring a system inherently changes that system. Thus, an eavesdropper trying to measure the quantum states used to generate the keys would unavoidably alter them, revealing their presence.
The experiment involves 5 nodes: two QKD equipments, one based in the Rectorat building, one in the PRECIS building in UPB.
Two other nodes, those that will perform the transfer (which we will call Alice and Bob),
are two stations in the same two buildings.
Alice is based in Rectorat and will have a direct point to point connection to the QKD equipment,
Bob is a station in PRECIS with a similar connection to its respective QKD equipment.
Finally, we use a broker server, with a known public IP, that will intermediate the transmission between Alice and Bob. The broker is needed due to security considerations,
as assigning public IPs to Alice and Bob poses risks to the infrastructure of their respective buildings.
A glimpse of the source code
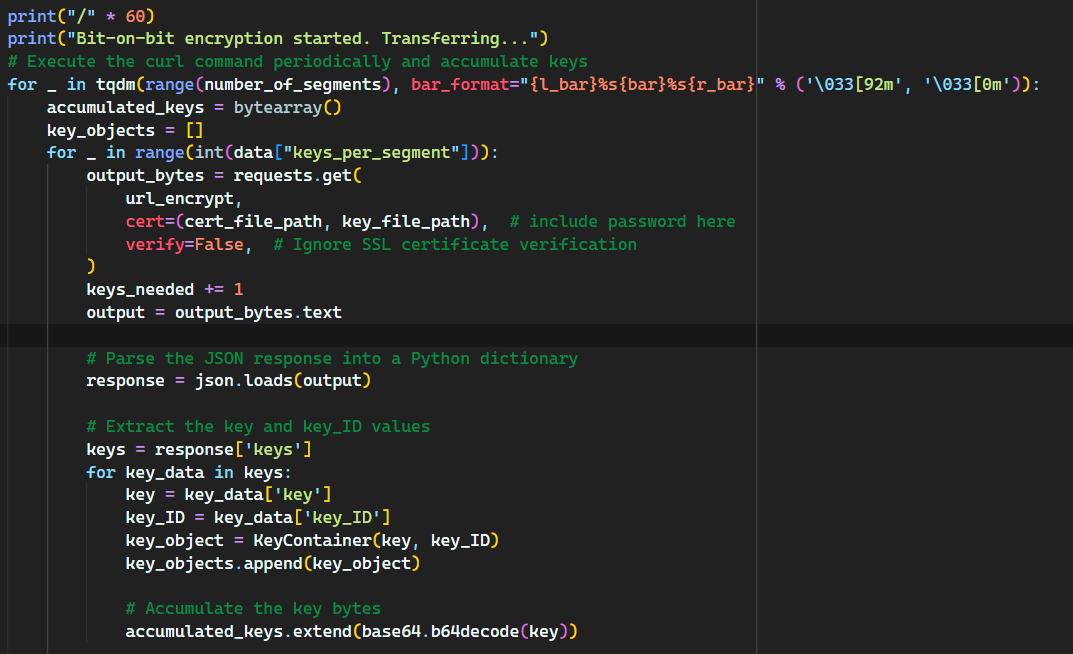
The source code/application/configuration is available upon reasonable request.

Application Interface
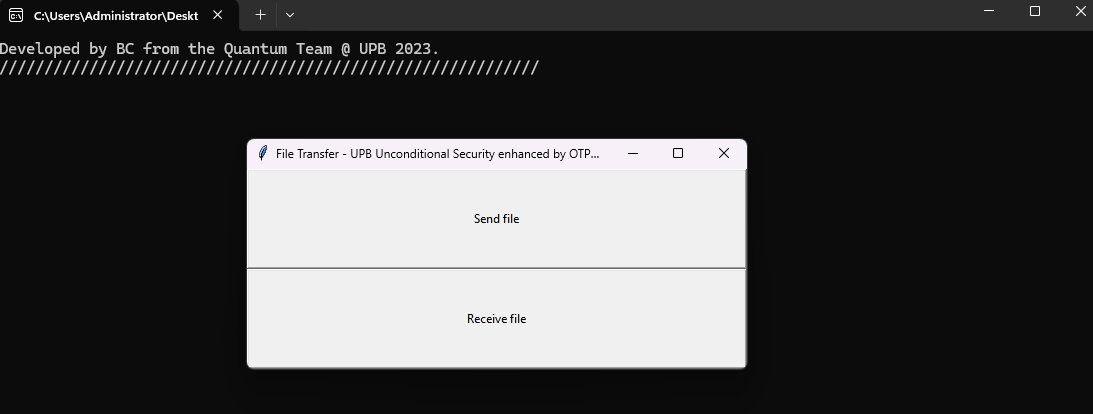
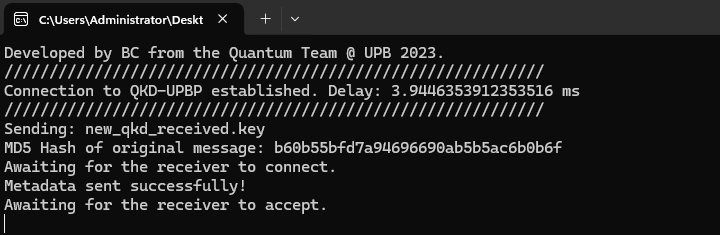
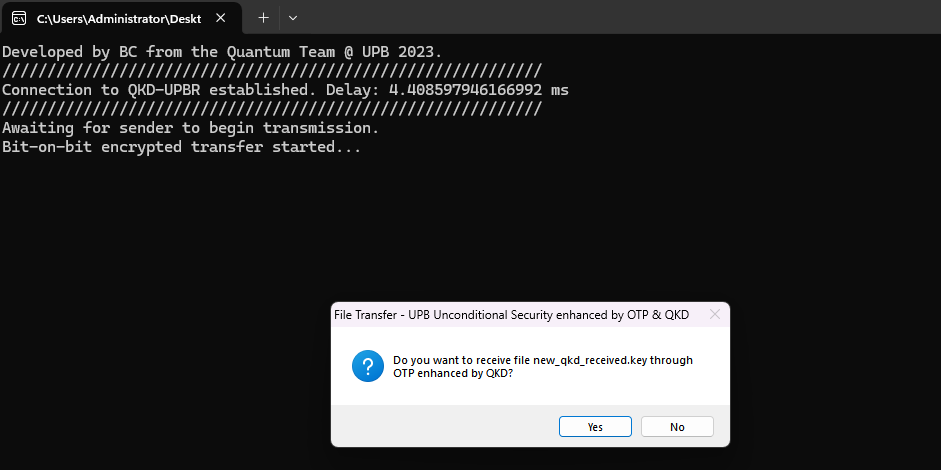
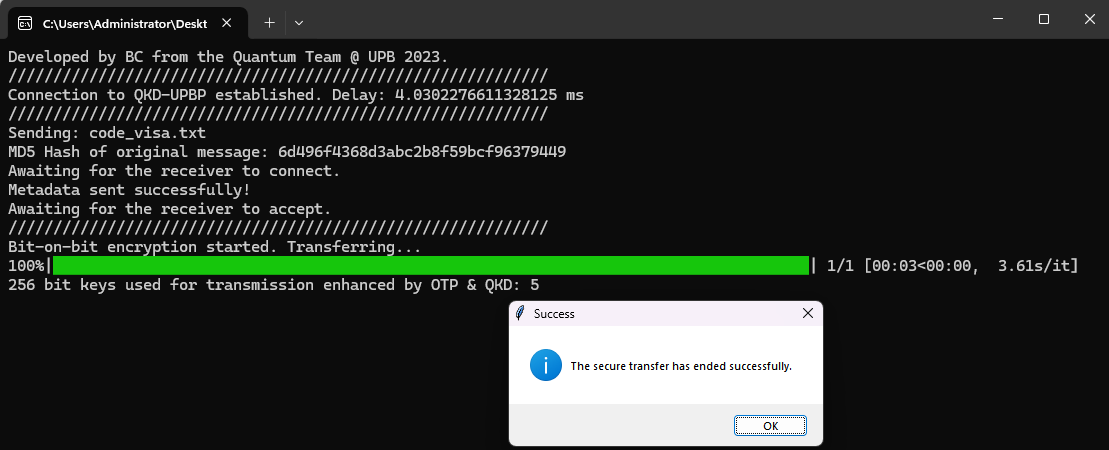
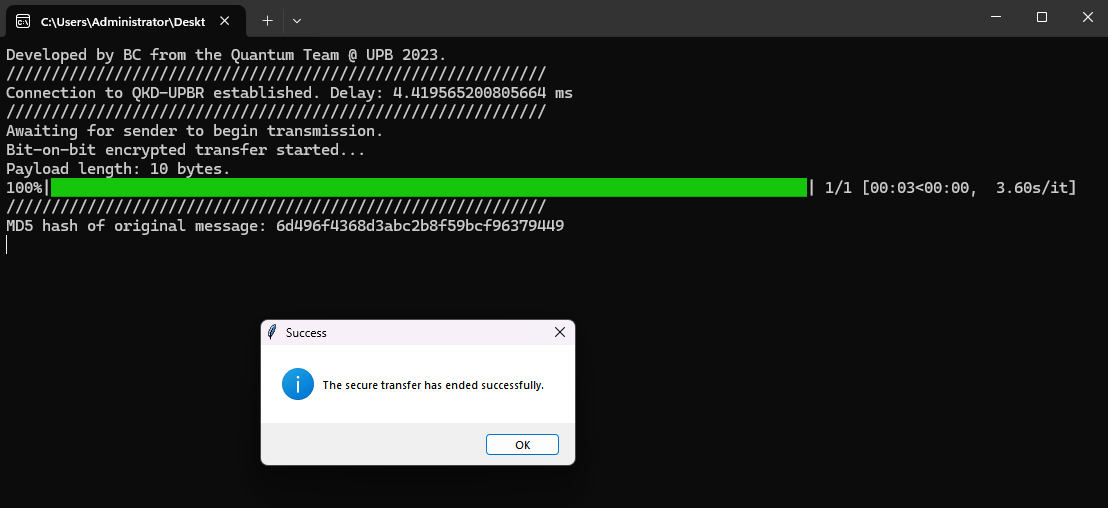
The Team Involved
The application was developed by Bogdan, coordinated by prof. PGP, and the network setup and configurations were done by Darius & Maria.






